DDoS Attacks : We are the victim of a targeted attack on our servers
Since the end of October 2023, DDoS attacks against our infrastructure have been on the increase, particularly against DE-03 and DE-04 machine, which is increasingly targeted by these attacks.
We do not know the origin of the attacks, nor the real motivations of the attacker. However, it is fairly obvious that the aim behind these attacks is to damage Lyd Hosting's business as a game server host.
The 12th November was marked by a major DDoS attack from 19:30 (UTC+1) to 23:10 on DE-03. We had to take drastic mitigation measures, which resulted in some of your players being unable to connect.
The aggressive anti-DDoS rules were lifted at 23:10 to allow everyone to regain access to the DayZ servers. This morning, we put in place less aggressive rules that should help us deal with future attacks.
Introduction
In this post, we'll try to explain the reasons why the current anti-DDoS system is ineffective and explain our new approach to combating these attacks in a fairly simple way.
We'll also tell you about the consequences: the main one being that the IPs used for your servers will have to be changed, step by step, before the final deployment of our solution.
Anti-DDoS protection
The current protection
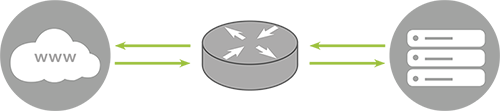
The current protection is provided by our service provider. The disadvantage of this protection is that it does not offer permanent filtering of network traffic, but rather mitigates attacks when they are detected.
Most of the attacks against us are short-lived, and our service provider's anti-DDoS protection has only been activated twice since the attacks began.
Graph: Traffic when no attack is detected
Graph: Filtering traffic when an attack is detected
When we launched our services, we chose to rely on this protection because the cost of alternatives was too high for our budget at the time. The new approach is quite innovative in that we will be able to protect our entire infrastructure.
The new protection
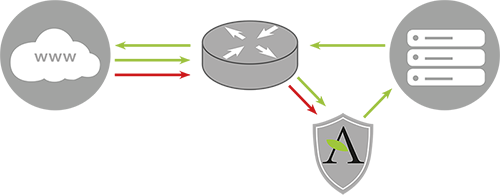
We are going to entrust a third-party company, specialising in the fight against DDoS attacks, with filtering the network traffic entering our network. To do this, we need to route the network traffic through the company's machines.
This means that a change of IP address is inevitable. This would have been necessary in all cases since the IP of our machines are known to the attacker, but with the new approach everything is different.
Indeed, this approach will enable us to mask the IP addresses associated with our servers. This will protect us from direct DDoS attacks aimed at bypassing our service provider's filter.
Graph: Permanent traffic filtering for each request
Explanations on deployment
We'd like to rush things to put these protections in place across our entire infrastructure, but it's pretty clear that we can't afford to do that. The consequences for our customers would be very negative.
The decision was taken to make the transition as smooth as possible, in stages, to enable our customers to inform their communities of the change so that they are as little affected by it as possible.
Phase 1: Configuration of GRE tunnels to our servers
This initial preparatory phase will be carried out during planned maintenance operations. It will have no impact on current servers and will enable us to start switching our customers over to the new IPs.
| Servers | Date |
|---|---|
| DE-01 | Deployed ✅ |
| DE-02 | Deployed ✅ |
| DE-03 | Deployed ✅ |
| DE-04 | Deployed ✅ |
| DE-05 | Deployed ✅ |
When phase 1 has been completed on the server where your service is located, we advise you to contact our teams to plan your switch to your new IP address.
Please note that the switchover does not mean the end of attacks. This "end" will come when the IPs we are currently using are definitively abandoned and replaced (see Phase 3).
Phase 2: Case-by-case switchover
Once phase 1 has been completed on the machines concerned, we will contact the customers on these machines to organise the IP address change. This stage will end at the start of phase 3.
Phase 3: Forced IP change on remaining services
This is the final stage, the one that will definitively confirm the switch to our new network approach. At this point, we will force the switchover to the new IP on servers that have not been switched over in time.
This is also the time when our service provider, in charge of hosting our servers, will be replacing the IPs of our servers. This will ensure that we no longer receive direct DDoS attacks on these machines.
| Servers | Date |
|---|---|
| DE-01 | Completed ✅ |
| DE-02 | Completed ✅ |
| DE-03 | Completed ✅ |
| DE-04 | Completed ✅ |
| DE-05 | Completed ✅ |
We would like to thank you sincerely for the understanding you have shown us. Not one customer was unpleasant and everyone understood that we were as much a victim as you were.
Soon, this period will be a bad memory and we will have increased the resilience of our infrastructure to this type of attack. The final phase of our fight has begun, so let's keep moving forward and never look back.
Rémi GAFFET
Founder of Lyd Hosting
